
The Need for Workload Identity in the Private Cloud
A growing consideration for cloud spending and the proliferation of AI have caused many organizations to evaluate their use of the public cloud. Many …

Solutions architect specializing in automation & orchestration. Interested in configuration management, CI/CD pipelines, infrastructure as code (IaC), and orchestrating disparate pieces of automation.

A growing consideration for cloud spending and the proliferation of AI have caused many organizations to evaluate their use of the public cloud. Many …

Jenkins is a popular open source CI server and many that are familiar with it often have a bit of a love/hate relationship. That being said, it is an …
With everything being defined as code nowadays, there’s a need for a place to store and version that code. The popular selection would be a …

AI is dominating most tech and even non-tech conversations nowadays with no signs of it slowing down anytime soon. This was certainly evident based on …
One of the technologies that I find the most enjoyable working with are orchestration solutions that are used to stitch together complex processes. …

VMware recently presented at the Tech Field Day Extra event during VMware Explore 2023. The presentation covered VMware’s networking and …
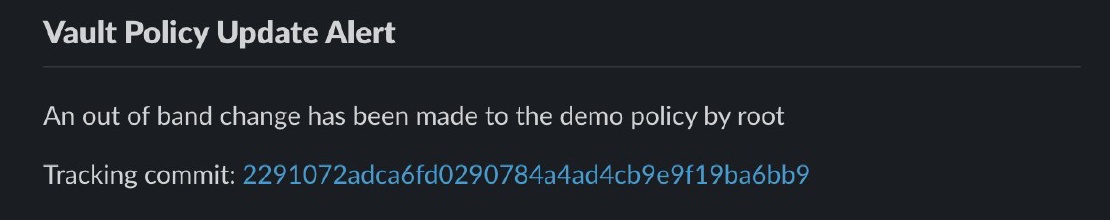
Security of a HashiCorp Vault deployment is of paramount importance given the sensitive nature of the information contained within the platform. …

How do we verify that the Terraform binary we download is the same as the one HashiCorp produced? Ensuring the integrity of software is important to …

Signing software has become critically important given the recent supply chain attacks. How do we verify that the software we’re downloading is …

Containerization and Kubernetes have dominated the IT conversation for the last handful of years. Containers enable rapid development, application …

One of the major benefits of using the public cloud is the integrated identity and access management (IAM). This simplifies the process of granting …
HashiCorp Vault supports several authentication methods for human and non-human access. Several of the non-human authentication methods are tied to …

Network booting operating systems isn’t a new concept and has been around for years. Bare metal deployments are typically where network booting is …

HashiCorp Vault supports a number of authentication methods including methods that utilize what HashiCorp refers to as a “trusted …

The VMware Event Broker Appliance (VEBA) fling is a really interesting project that enables administrators to take advantage of event driven …

I have made the decision to become the director of technical marketing at Morpheus Data and I start that new position today. Morpheus Data is a …

Chaos Engineering is the practice of experimenting or injecting faults into a system to test how the system responds to the failure …
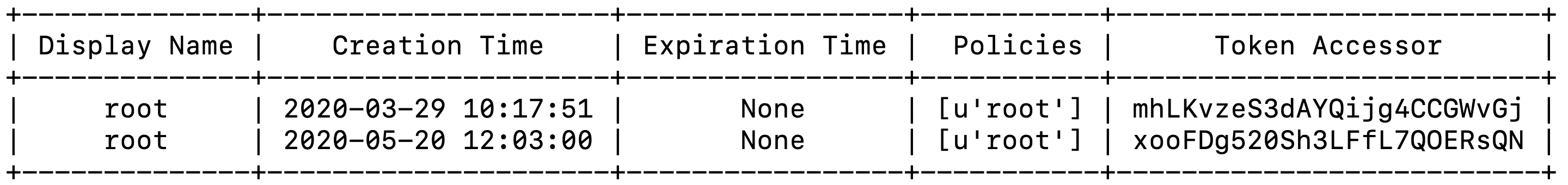
Revoking the root token on a production HashiCorp Vault deployment is one of the recommended best practices for securing an instance of HashiCorp …

HashiCorp Vault generates a default root token during installation and best practice dictates that the token should be revoked once the deployment has …

Security of a HashiCorp Vault deployment is of paramount importance given the sensitive nature of the information contained within the platform. …

In this blog post we’ll look at the HashiCorp Vault plugin for Puppet Bolt that enables authentication credentials for Bolt to be retrieved from …

HashiCorp Terraform is a popular Infrastructure as Code (IaC) tool that is used for provisioning virtual machines or cloud instances along with other …
Treating workloads as “cattle” or immutable is a popular management paradigm for stateless workloads and is especially prevalent for such …
Template management is a critical facet of infrastructure management and traditionally one of the more challenging operations there is. The advent of …
HashiCorp Terraform 0.12.2 added official support for a Puppet provisioner. One caveat is that the provisioner is only available in 0.12.x of …
I’m now in my second week at Puppet which is best known for its configuration management software that shares the same name as the company. …
I gave a talk for HashiCorp’s HashiDays event earlier this year that centered around operational intelligence for HashiCorp Vault. The focus was …
HashiCorp Vault is quickly becoming the defacto secrets management platform used in environments that rely on DevOps concepts for application …

NetApp was one of the “legacy” companies that presented a number of compelling solutions at Cloud Field Day #3. The challenge for many …

Earlier this month I had the privilege of being a delegate for Cloud Field Day 3 (http://techfieldday.com/event/cfd3/) which is a tech event put …

Vault (https://www.vaultproject.io/) is a secrets management tool created by HashiCorp that is extremely popular. Given the sensitive nature of the …
A very popular Terraform state management configuration is to utilize AWS S3 for state management and AWS DynamoDB for state locking. The problem is …
What is immutable infrastructure? Immutable infrastructure is the concept of utilizing an infrastructure component in an ephemeral manner. This means …

In a previous post we walked through configuring a PostgreSQL database server as the external database for our vRealize Orchestrator (vRO) cluster. In …
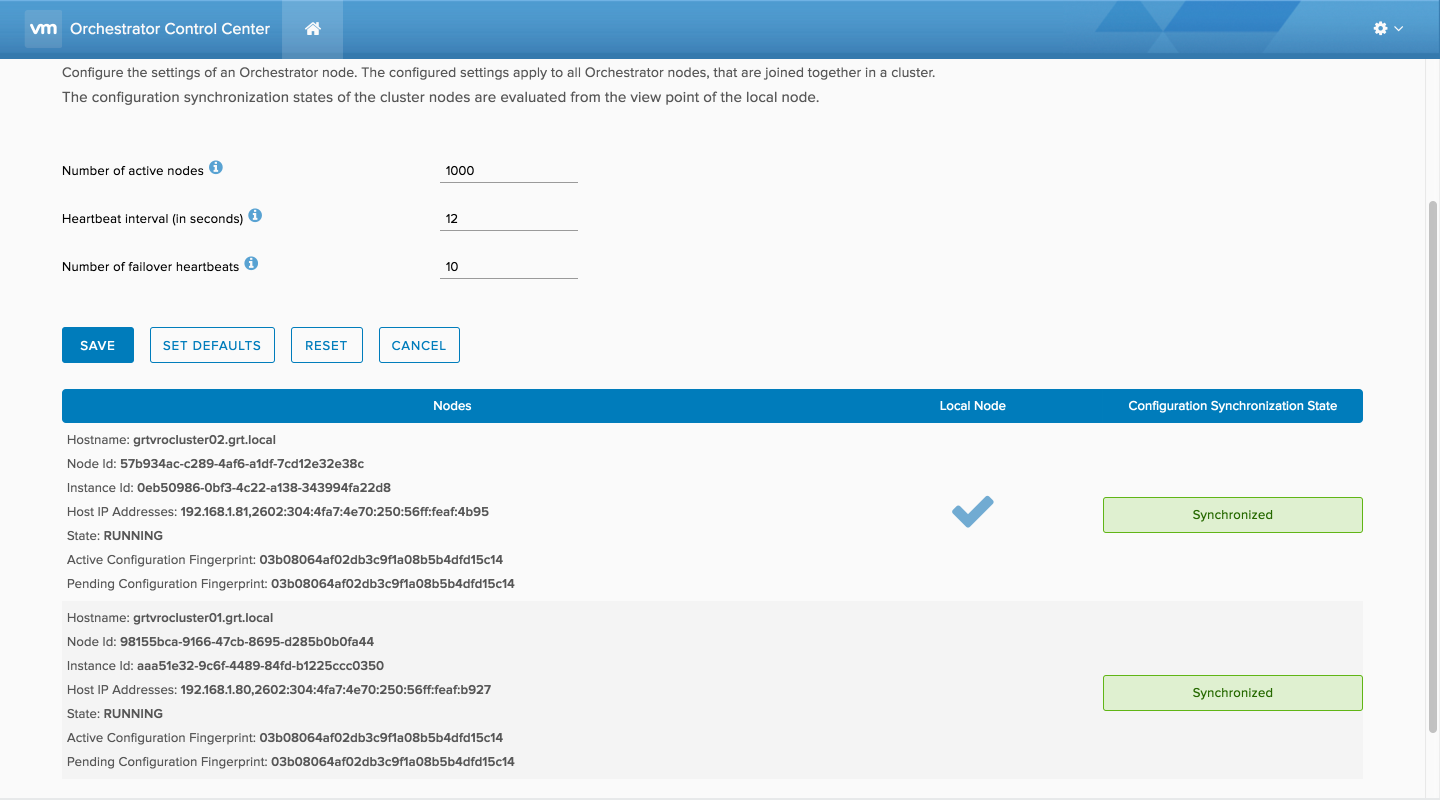
In this post we’re going to build out a two node vRealize Orchestrator cluster with a PostgreSQL database. VMware is deprecating support for …

In this post we’re going to walk through how to dynamically populate a vRA request field using values retrieved from a REST API using vRO. A …

In this post we’ll walk through how we can utilize vRealize Orchestrator and Splunk to determine how compliant our vRA appliance is with the …

A recent blog post by Rob Nelson about using vRO to provision VMs with vSphere tags …
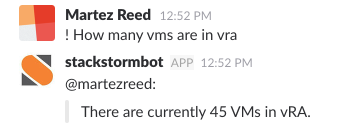
ChatOps is a pretty cool and still emerging technology that allows users to initiate actions on external systems from within a messaging platform such …
What is Policy Based Autosigning A critical aspect of any Puppet deployment is determining how we want to allow nodes to get their certificate signed …
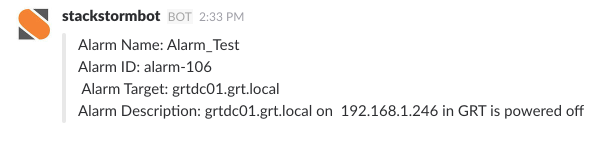
Being notified of when something happens in your environment has always been important and has evolved over time from basic emails to IM messages via …
This post covers the section listed below on the Certified Jenkins Engineer (CJE) exam. Section #3: Building Continuous Delivery (CD) Pipelines …
Docker (https://www.docker.com/) is arguably the most popular container platform and this post covers a number of useful Docker commands from basic …
This post covers the section listed below on the Certified Jenkins Engineer (CJE) exam. Section #1: Key CI/CD/Jenkins Concepts Fingerprints What are …
Recently a co-worker of mine (Thanks Ken Erwin) introduced me to Jenkins Job Builder (http://docs.openstack.org/infra/jenkins-job-builder/) which is a …

This post covers integrating Jenkins CI server with Microsoft Active Directory to provide centralized authentication. Step #1 - Install he Active …

Puppet supports various hiera backends to pull in external data from various sources. This post will cover integrating open source puppet with a …